CryptoWall 4.0 released with new features such as Encrypted File Names.
See “What is CryptoWall” at the end of this post.
CryptoWall 4.0 has been released that displays a redesigned ransom note, new file names, and now encrypts a file’s name along with its data.

Ransom Note
For those who may have become infected by this variant, you can visit the dedicated CryptoWall 4.0: Help_Your_Files Ransomware Support Topic to discuss the infection or receive support on it.
The most significant change in CryptoWall 4.0 is that it now also encrypts the file names of the encrypted files. Each file will have its name changed to a unique encrypted name like 27p9k967z.x1nep or 9242on6c.6la9. The file names are probably encrypted to make it more difficult to know what files need to be recovered and to make it more frustrating for the victim.

Folder containing Encrypted Files
Below are two examples of the emails:
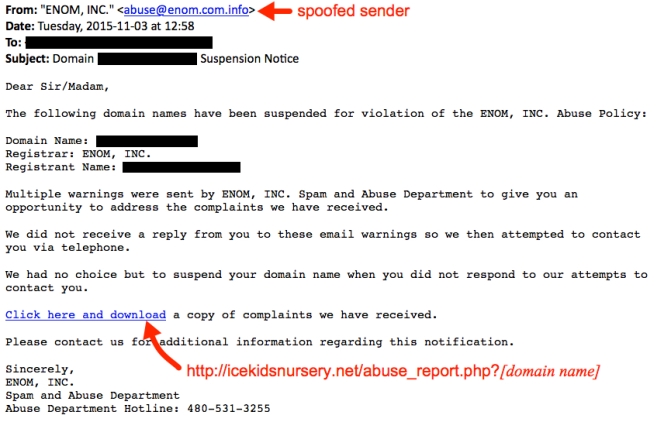

If you receive one of the emails, the link follows a specific pattern: [unrelated compromised website]/abuse_report.php?[your domain name]. The domain names are not important. You can always get the malware by substituting any string of characters for the domain name in the URL (assuming no one has fixed the compromised website yet).

Shown above: Substituted a string of “X”s for the domain name in a URL from one of the emails.
Final Words
If you receive one of these emails, and you download the file, you should see plenty of warnings the file is not safe. In a company environment, properly-administered Windows hosts should prevent people from running the malware.
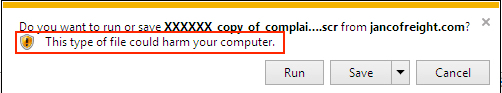


In my personal opinion, this mal-spam isn’t a serious threat if you are aware that it is out there. So why do criminals run these campaigns? Apparently, enough of their emails get through, people still fall for the allure of clicking links and opening random email attachments, and their Windows computers are configured so they can run it.
I recommend that you keep your antivirus solution always on and UP-TO DATE! It can be used as an additional layer of protection for you systems.
If you have a bad habit of clicking/opening random links and attachments, Bitdefender Labs has developed a vaccine that allows users to immunize their computers and block any file encryption attempts, even if they become infected with CryptoWall, one of the most powerful clones of the Cryptolocker malware.
As usual, I have NOT tested this software for effectiveness. So use at YOUR OWN RISK.
Bitdefender advises customers to run a fully dedicated Internet Security solution such as those provided by Bitdefender to protect against all threats. The CryptoWall Immunizer is only effective in protecting systems that may get infected with versions one and two of the Cryptowall ransomware at this point in time.
What is CryptoWall?
Cryptolocker and its public-private key encryption mechanism has become a huge financial success for its creators. Its high turnaround prompted other cyber-criminal entities to write copycats that use much more sophisticated spreading and encryption algorithms. Some of the most notorious families of ransomware now wreaking havoc include CryptoWall, Citroni and TorLocker. Android users were also massively targeted by ransomware throughout 2014.