Microsoft is using Win7 and 8.1 updates to enable and re-enable unwanted upgrades
http://www.computerworld.com/article/3012278/microsoft-windows/microsoft-sets-stagefor-massive-windows-10-upgrade-strategy.html
Saying “Dramatically Increased Connectivity” over and over is too laborious, thus: “DIC”
I am not saying that Windows 10 is necessarily a bad thing. But, If you don’t want it, it should not be forced on you.
In the wake of Windows 10 DIC, we’ve seen the creation of many freeware apps to assist users in managing Windows 10 DIC, because they feel rather strongly about not wanting to have any DIC… Regardless of what that DIC’s purpose and intentions may be.
Another large group of people has decided that rather than getting Windows 10 and then working to neuter the DIC, they would prefer to simply remain on Windows 7 or 8.1. This has spawned another class of freeware to prevent Microsoft from shoving Windows 10 down everyone’s throat. One such tool is that GWX Control Panel by Josh Mayfield
(GWX == Get Windows 10)
- Formerly “GWX Stopper” renamed to the GWX Control Panel
- Updated on November 24th to run continuously in the background to periodically check the Windows GWX settings:
- http://ultimateoutsider.com/downloads/ (installer or stand-alone)
Since Windows 10’s release, and thanks to his GWX Control Panel and users, Josh has been monitoring Microsoft’s GWX behavior.
http://blog.ultimateoutsider.com/2015/08/using-gwx-stopper-to-permanently-remove.ht ml
Josh: “December 1, 2015: I’ve gotten some very interesting reports from people using the new Monitor Mode feature. Different PCs are seeing different Windows 10 settings get re-enabled for mysterious reasons. They’re not false alarms; these settings are really getting re-set by Windows (it’s not happening to everybody, just certain users/computers), and I’m doing research and testing to see what I can do to stop it once and for all. To those of you observing this strange behavior: Hang in there; the next version of the GWX Control Panel will have some features intended to help you regain control and better understand what’s happening on your PC.”
The Windows Update engine has been updated and the December 1st release says:
- “This update enables support for additional upgrade scenarios from Windows 7 to Windows 10, and provides a smoother experience when you have to retry an operating system upgrade because of certain failure conditions. This update also improves the ability of Microsoft to monitor the quality of the upgrade experience.”
- ComputerWorld writes that <quote> In late October, Terry Myerson, the Microsoft executive who runs the Windows and devices teams — dubbed the “More Personal Computing” group — outlined how Microsoft would try to convince users of Windows 7 and 8.1 to upgrade to Windows 10. Rather than wait for customers running the older editions to request a copy of the new OS — the original idea from the summer — Microsoft will instead begin to automatically send the upgrade to PCs via Windows Update, the default security maintenance service.
- Gregg Keizer , writing for ComputerWorld continues: <quote> The new push will be a two-step process, with the first kicking in this year, the second in early 2016. First, Microsoft will add the Windows 10 upgrade to the Windows Update list on Windows 7 and 8.1 systems as an “optional” item. That list can be examined by users, letting them choose — or not — each optional update.
Sometime next year (2016), 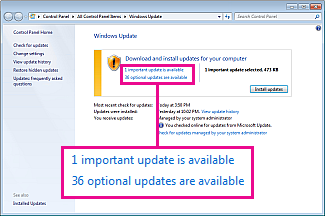 Microsoft will shift the Windows 10 upgrade
Microsoft will shift the Windows 10 upgrade
from the optional ‘nag’ to the “recommended” or “Important” update list. Which means, rather than seeing the “Upgrade to Windows 10” popup nag, you will see it in your “Recomended” or “Important” update list along with all of your other Windows Updates.
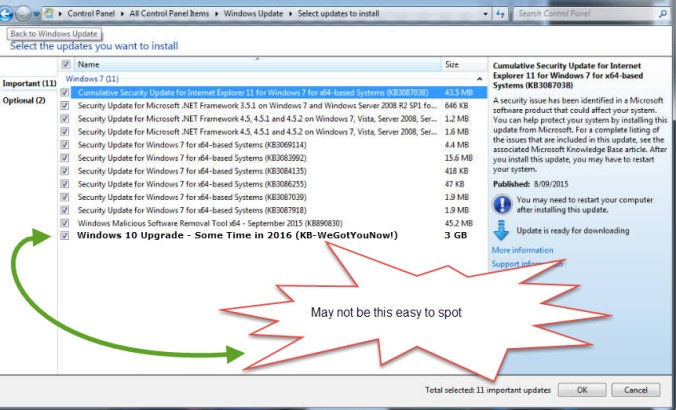
Updates on that list are automatically downloaded and installed on most PCs. If you have the “Auto Update” feature turned on, then you will very likely be automatically “Upgraded” to Windows 10.
The GWX Control Panel app can be downloaded from Mayfield’s website.
The App is free, but Mayfield does accept donations through PayPal. Gregg Keizer, who interviewed Josh quoted him, saying: I get a donation from about one in every thousand downloads.
 Microsoft will shift the Windows 10 upgrade
Microsoft will shift the Windows 10 upgrade